As we step further into the digital age, the security landscape continues to evolve at an unprecedented pace. According to a recent study by ISC Security Solutions, the global security industry is expected to reach a $430 billion by 2027. This explosive growth is fueled by advancements in technology and the constant need to bolster security measures. However, keeping pace with these rapid advancements often poses a challenge for businesses and individuals alike, potentially leaving them vulnerable to emerging threats.
To mitigate this, it’s crucial to stay informed about the latest trends, allowing you to make proactive security decisions and implement the most effective solutions to safeguard your assets. This blog explores the top trends that are shaping the security industry in 2024, empowering you to make informed decisions for a more secure future.
1. The Rise of Artificial Intelligence (AI) in Security
The security industry is witnessing a revolution driven by Artificial Intelligence (AI). AI is enhancing perception capabilities, leading to significant improvements in security systems.
- Enhanced Threat Detection: AI-powered video analytics can detect suspicious activity in real-time. Imagine a system that can automatically identify loitering individuals or objects left unattended in restricted areas, significantly reducing reliance on manual monitoring.
- Facial Recognition for Access Control: Facial recognition systems powered by AI can identify authorized personnel and deny access to unauthorized individuals attempting to enter secure areas. This adds an extra layer of security to traditional access control methods.
- Anomaly Detection for Cyber Threats: AI can analyze network traffic patterns and flag unusual activities that might indicate a cyberattack. This allows security teams to identify and respond to potential threats before they cause significant damage.
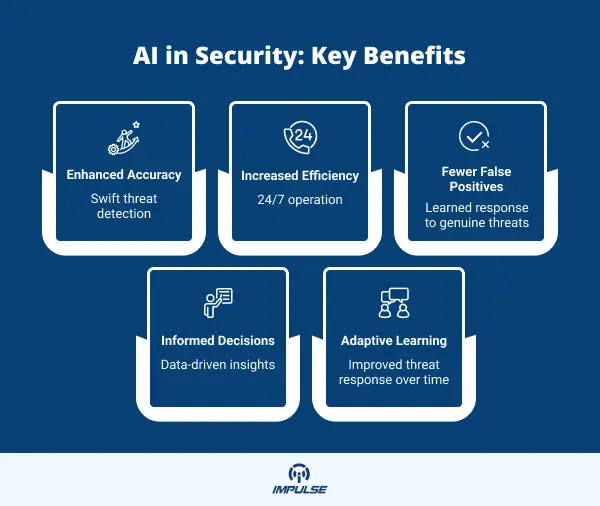
- Enhanced Accuracy in Threat Detection: AI drastically improves the accuracy of threat detection by swiftly analyzing data and identifying anomalies. This capability allows AI to detect threats that might be overlooked by human operators, thus significantly reducing the risk of undetected security breaches.
- Increased Efficiency: AI systems can work around the clock without fatigue, enhancing operational efficiency. This enables security personnel to focus more on strategic and critical tasks, rather than manual and time-consuming activities such as continuous monitoring.
- Reduction in False Positives: One of the significant issues in security operations is the high number of false positives that can lead to wasted time and resources. AI can help reduce these false positives by learning from past incidents and refining its algorithms to better differentiate between genuine threats and benign activities.
- Better Decision Making: AI can gather and analyze a vast amount of data, providing comprehensive insights that human analysis might miss. These insights can enhance the decision-making process for security personnel, making it more data-driven and effective.
- Adaptive Learning: AI systems have the advantage of being able to learn and adapt over time. This means that they can become more effective at identifying and responding to threats as they encounter more data and situations, continually enhancing the security posture of an organization.
Also Read: Top 5 Outdoor Network Cameras for Businesses: Deter Crime and Monitor Property
2. The Maturing of the Internet of Things (IoT) Security Landscape
The Internet of Things (IoT) is transforming how we live and work. Smart devices, from security cameras and access control systems to environmental sensors and smart locks, are becoming increasingly common. While these devices offer convenience and automation, they also introduce new security vulnerabilities.
- Potential Vulnerabilities: A growing network of interconnected IoT devices can introduce security risks if not properly secured. Weak security protocols, outdated firmware, and lax password management practices can leave these devices vulnerable to hacking.
- The Trend Towards More Secure IoT Solutions: Fortunately, the security landscape for IoT devices is maturing. Manufacturers are prioritizing security features like:
- Secure data encryption to protect sensitive information transmitted between devices.
- Regular firmware updates to address security vulnerabilities and improve functionality.
- Strong password management practices to prevent unauthorized access.
By implementing these security measures, manufacturers and users can create a more secure and trustworthy IoT ecosystem.
3. The Growing Importance of Cybersecurity
Cyberattacks are a constant threat in today’s digital world. Businesses and individuals alike are increasingly targeted by ransomware attacks, phishing scams, and data breaches. Here’s how you can improve your cybersecurity posture:
- Employee Training: Implement cybersecurity training programs to educate your staff on how to identify and avoid cyber threats. Phishing scams are often sophisticated, and a well-trained workforce is your first line of defense.
- Software Updates: Regularly update software and applications with the latest security patches. These updates often address newly discovered vulnerabilities, making it more difficult for attackers to exploit them.
- Endpoint Protection: Utilize endpoint protection software to detect and prevent malware infections on devices. This software can act as a safety net, catching threats that might slip through other security measures.
By following these tips and staying informed about the latest cyber threats, you can significantly improve your organization’s cybersecurity posture.
Also Read: Futureproof Your Business: A Smart Guide to Choosing Video Surveillance for Tomorrow
4. The Integration of Cloud-based Security Solutions
Cloud-based security solutions are gaining traction due to several advantages over traditional on-premise systems. Here’s what makes cloud security so attractive:
- Scalability: Cloud-based security solutions offer easy scalability. You can adapt your security infrastructure to meet changing needs without significant hardware investment.
- Accessibility: Remotely monitor and manage your security system from any internet-connected device. This allows for greater flexibility and improved response times to security incidents.
- Automatic Updates: Cloud-based security solutions benefit from automatic software updates and security patches. This ensures your system remains protected against evolving threats without manual intervention.
Cloud security offers a compelling solution for businesses of all sizes looking for a scalable, accessible, and up
Also Read: The Ultimate 2024 Guide to Outdoor CCTV Video Surveillance Systems
The Integration of Cloud-based Security Solutions
Cloud-based security solutions are becoming increasingly popular and are quickly becoming a standard in the security industry, replacing traditional on-premise systems. There are several reasons why these cloud solutions are becoming so attractive:
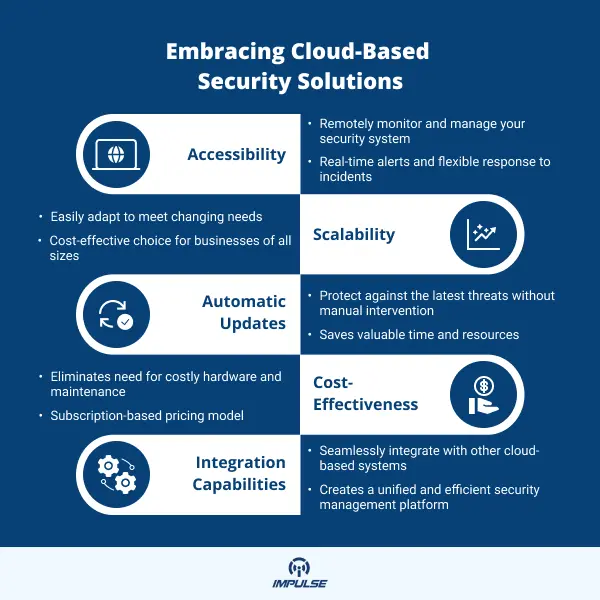
- Scalability: One of the main advantages of cloud-based security solutions is their scalability. Traditional security systems often require significant hardware investment to scale up as your business grows. However, cloud-based solutions can easily adapt to meet changing needs, whether you’re adding new users or incorporating additional security features. This scalability makes cloud-based systems a cost-effective choice for both small businesses and large corporations.
- Accessibility: Cloud-based security solutions provide the ability to remotely monitor and manage your security system from any internet-connected device. This can be particularly beneficial for businesses with multiple locations or for those who need to access their systems while on the go. With real-time alerts and the ability to respond to incidents from anywhere, cloud-based solutions offer greater flexibility and improved response times to security incidents.
- Automatic Updates: One of the key benefits of cloud-based security solutions is the automatic software updates and security patches. With traditional systems, these updates often require manual intervention, which can be time-consuming and can leave your system vulnerable if not regularly updated. However, cloud-based solutions automatically update to protect against the latest threats. This not only ensures that your system remains secure but also saves your team valuable time and resources.
- Cost-Effectiveness: Cloud-based solutions can often be more cost-effective than traditional on-premise systems. They eliminate the need for costly hardware and maintenance, and the subscription-based pricing model can be more manageable for many businesses.
- Integration Capabilities: Cloud-based security solutions can seamlessly integrate with other cloud-based systems. This could include your video surveillance, access control, and alarm systems, creating a unified and efficient security management platform.
By leveraging these advantages, cloud security offers an appealing solution for businesses of all sizes. Whether you’re a small business looking for a flexible, affordable security solution, or a large corporation needing to manage multiple locations, cloud-based security is a top contender for a scalable, accessible, and up-to-date security strategy.
Also Read: Empower Your Security: Setting Up a CCTV Pole System – Tips and Tricks
5. The Importance of Biometric Authentication Technologies
Biometric authentication technologies, like fingerprint scanners and facial recognition systems, are becoming increasingly common in security applications. These systems offer several advantages over traditional methods like passwords or key cards.
- Enhanced Security: Biometric identifiers, such as fingerprints or facial features, are unique to each individual. This makes them a more secure method of authentication compared to passwords, which can be easily guessed or stolen.
- Improved Convenience: Biometric authentication eliminates the need to remember complex passwords or carry key cards. This provides a more user-friendly security experience.
- Reduced Risk of Unauthorized Access: Biometric data cannot be easily shared or replicated, unlike passwords. This significantly reduces the risk of unauthorized individuals gaining access to secure areas.
While biometric authentication offers significant benefits, it’s crucial to consider potential privacy concerns and ensure these systems are implemented ethically and responsibly.
6. The Rise of Advanced Physical Security Measures
Advanced physical security measures are an integral part of any effective security strategy. Here’s a more detailed look into some of the recent advancements in this field:
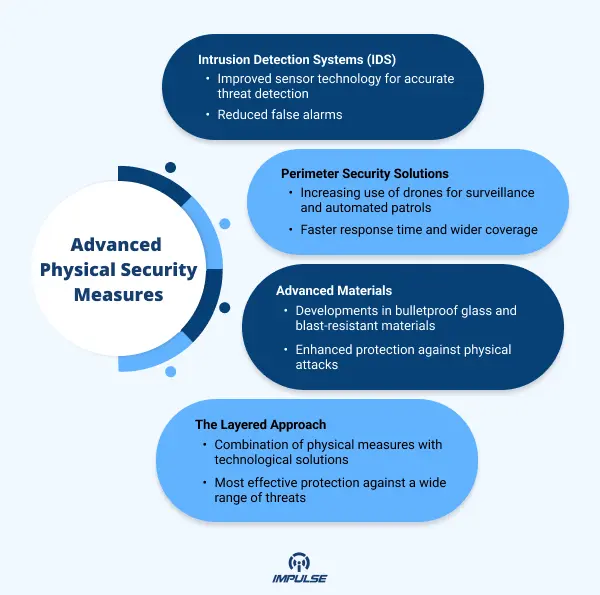
- Intrusion Detection Systems (IDS): Intrusion Detection Systems have seen significant advancements, particularly in the realm of sensor technology. These improved sensors are now capable of more accurately detecting threats, making them an essential part of any security system. Imagine, for example, motion detectors that have the capacity to distinguish between a genuine security breach and a small animal wandering onto your property. This level of specificity in threat detection can drastically reduce false alarms, making security systems more reliable and effective.
- Perimeter Security Solutions: The use of drones for security purposes is on the rise. They are being increasingly employed for aerial surveillance and automated patrols of large perimeters. This use of technology allows for a more comprehensive security presence, covering larger areas than would be feasible with human patrols alone. Moreover, drones can respond more quickly to security incidents, reducing the response time and potentially preventing security breaches.
- Advanced Materials: The material sciences field has contributed to security measures, with developments in bulletproof glass and blast-resistant materials. These advanced materials are constantly being improved to provide enhanced protection against physical attacks. This progress not only increases the physical barrier between potential threats and the assets you’re protecting but also provides peace of mind knowing your defenses are robust.
Incorporating these advanced physical security measures into your strategy is part of a layered approach. This approach combines these physical measures with technological solutions like access control systems, video surveillance, and AI-powered analytics. This comprehensive strategy ensures the most effective protection against a wide range of threats.
Also Read: Exploring Different Camera Types: Dome, Bullet, PTZ, and Box Cameras for Various Surveillance Needs
7. A Growing Focus on Privacy and Data Security Regulations
In the current digital era, data privacy and security are becoming increasingly significant on a global scale. Prominent regulations such as the General Data Protection Regulation (GDPR) in the European Union (EU) and the California Consumer Privacy Act (CCPA) in the United States (US) are enforcing stricter obligations on how businesses gather, utilize, and preserve personal information.
These governmental regulations are not just legal obligations but also serve as a framework for businesses to prioritize data protection and privacy. Their primary goal is to ensure businesses respect the privacy of individuals and protect their personal data from misuse or unauthorized exposure./
- Impact on Security Practices: These regulations necessitate that businesses inculcate robust data security measures to safeguard personal information. This involves the implementation of secure data storage systems, robust encryption methods, and stringent access controls to prevent unauthorized access. Businesses are also required to have protocols in place to promptly identify and respond to data breaches, which includes notifying affected individuals and relevant authorities. Furthermore, businesses need to ensure they have policies in place to prevent the misuse of personal data, whether it’s by employees, third-party vendors, or malicious actors.
- Transparency and Control: Alongside enhancing security practices, these regulations also dictate that organizations must maintain transparency about their data practices. This means businesses need to clearly communicate to individuals how their personal data is being collected, used, and stored. Often, this is achieved through comprehensive privacy policies that are easily accessible and understandable. Moreover, these regulations empower individuals with more control over their personal data. This includes the right to access their information, correct any inaccuracies, and erase their data under certain circumstances.
- Accountability and Compliance: These regulations also introduce a higher level of accountability for businesses. Organizations are expected to demonstrate their compliance with these regulations, which can include maintaining detailed records of data processing activities, conducting regular data protection impact assessments for high-risk processing activities, and appointing a designated data protection officer in certain cases. Non-compliance can result in hefty penalties, which can be financially crippling for businesses.
While these regulations can seem complex and challenging to navigate, they ultimately serve to foster a more secure digital environment for all. By adhering to these regulations, businesses not only ensure they’re on the right side of the law, but they also instill trust in their customers and stakeholders, demonstrating their commitment to protecting their valuable data.
In conclusion, privacy and data security regulations are becoming a cornerstone in the evolving security landscape. It’s more important than ever for businesses to understand and comply with these regulations as part of their overall security strategy.
Also Read: Protecting Your Assets: Industrial Security Camera Solutions
Conclusion
In an ever-changing world, the security industry is continually evolving. This evolution is propelled by advancements in technology and the need to tackle new threats. Keeping abreast of the latest trends is not just beneficial, but crucial. It empowers you to make proactive decisions, thereby implementing a security strategy that is future-proof and robust.
By comprehending these trends and integrating them into your security strategy, you can foster a safer environment. This enhanced security benefits your business, your employees, and your customers, creating a sense of trust and safety.
At Impulse- the best security camera, we are here to assist and partner with you in safeguarding your assets. Together, we can navigate the dynamic security landscape and construct a future that is safer and more secure.
Security is an ever-evolving landscape, and staying up-to-date with the latest trends is crucial for safeguarding your assets. We at Impulse are committed to helping you navigate this dynamic environment and implement a robust, future-proof security strategy.


