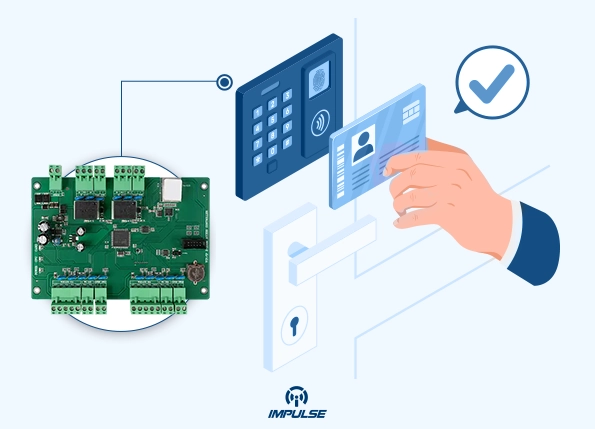
The Modern Security Challenge
Organizations face unprecedented challenges in protecting their assets, information, and personnel. Traditional lock-and-key systems are increasingly inadequate against sophisticated threats and operational demands. Businesses, healthcare facilities, educational institutions, and government buildings require solutions that balance security with accessibility while maintaining operational efficiency.
The modern workplace demands systems that can manage varying access privileges across different zones, maintain detailed entry logs, and respond dynamically to emergency situations—all while integrating seamlessly with existing infrastructure. This complex need has given rise to specialized security solutions like two door access control systems.
What is a Two Door Access Control System?
A two door access control system is a specialized security solution designed to manage and restrict access through two separate entry points using electronic authentication methods. Unlike traditional single-door systems, these advanced configurations allow organizations to implement comprehensive security protocols that control the flow of individuals between interconnected spaces.
Why Organizations Need Advanced Access Control Solutions?
Security Vulnerabilities of Traditional Systems
Traditional security methods present numerous weaknesses:
- Physical keys present significant security risks as they can be easily lost, stolen, or duplicated by unauthorized individuals, potentially compromising entire security systems
- Traditional systems lack comprehensive logging capabilities, making it impossible to track and monitor who accessed specific areas and at what times, which is crucial for security audits
- When security is compromised, traditional systems offer no quick way to revoke access privileges, requiring time-consuming and costly lock changes
- Managing access for temporary visitors, contractors, or guests becomes a complex logistical challenge without digital credentials and automated systems
- Legacy security systems often operate in isolation, preventing integration with modern security technologies and building management systems
Regulatory Compliance Requirements
Many industries face strict regulatory requirements regarding access control:
- Healthcare facilities must implement robust access control systems to comply with HIPAA security rules, protecting sensitive patient information and restricted areas
- Financial institutions need to meet comprehensive PCI DSS requirements to secure payment data and maintain strict access controls to sensitive financial areas
- Government contractors are required to implement FISMA compliance measures, ensuring proper security controls for federal information systems and assets
- Manufacturing facilities must adhere to OSHA safety standards for restricted areas, implementing proper access controls to protect workers and sensitive equipment
Advanced Threat Landscape
Today’s security threats have evolved beyond what basic systems can handle:
- Sophisticated tailgating techniques and coordinated unauthorized access attempts require advanced detection and prevention systems
- Modern social engineering attacks combine physical and digital techniques to breach security, requiring integrated defense mechanisms
- Emergency situations demand immediate facility-wide lockdown capabilities with automated responses and notifications
- Contemporary health and safety protocols require advanced contact tracing capabilities and real-time occupancy management systems
Also Read: Expert Tips for Installing Your CCTV Camera System
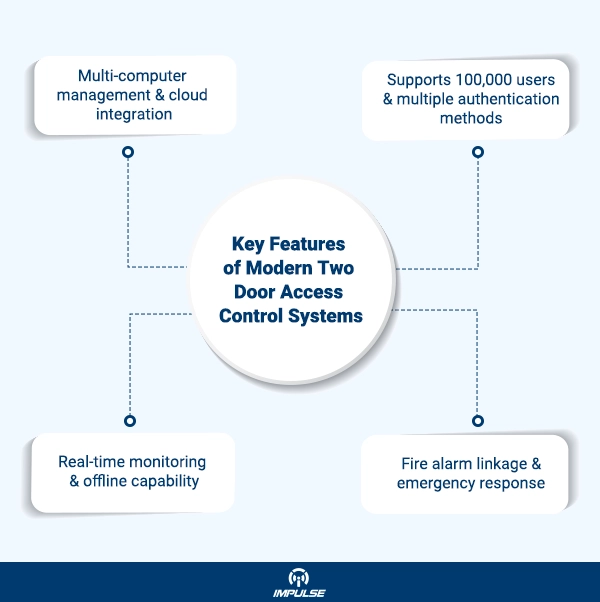
Key Features of Modern Two Door Access Control Systems
Multi-Authentication Methods
Modern access control systems have evolved to support a diverse range of authentication mechanisms, providing unprecedented flexibility and security. These systems can be configured to require single or multiple forms of verification, depending on the security requirements of different areas or times of day.
The system supports RFID card readers that provide quick, contactless access using encrypted card technology. PIN codes offer an additional layer of security through knowledge-based authentication, while biometric verification utilizing fingerprint and facial recognition provides foolproof identification through unique physical characteristics. Mobile credentials via smartphone apps enable convenient, secure access through personal devices, and QR and dynamic 2D code technology is perfect for temporary access and visitor management.
Interlocking Door Capabilities
A critical feature of two door access control systems is the sophisticated ability to create mantrap or airlock configurations. These specialized setups provide enhanced security through controlled sequential access, making them invaluable for high-security environments.
The system prevents tailgating by ensuring one door must close before the second opens, maintaining strict access control. It creates security vestibules for high-security areas requiring extra protection measures, while enabling clean room protocols for specialized manufacturing environments where contamination control is crucial. Additionally, it provides containment capabilities for sensitive areas requiring strict access management.
Centralized Management
Modern enterprise-grade systems offer comprehensive management capabilities through a centralized platform. This unified approach streamlines security operations and provides administrators with powerful tools to maintain optimal security levels across the facility.
The system provides unified administration of multiple entry points from a single interface, along with regional interlocking configurations for complex facility management. User privilege management is handled from a central console with role-based access control, and the system integrates seamlessly with HR systems for automatic access provisioning and de-provisioning based on employment status.
Real-Time Monitoring and Reporting
The system provides comprehensive real-time monitoring capabilities that enable security personnel to maintain constant awareness of facility access activities. These advanced monitoring features help organizations maintain security compliance and respond quickly to potential threats.
Live status dashboards show real-time access activities and system health, while comprehensive audit trails enable detailed activity tracking and investigation. The system includes sophisticated automated alert systems for suspicious activities and security breaches, complemented by custom reporting capabilities for compliance documentation and security analysis.
The Impulse Two Doors Access Control System
The Impulse 2 Doors Access Control System represents the cutting edge of two door access control technology. This TCP/IP-based system offers comprehensive security management for two separate doors while providing extensive integration capabilities with existing infrastructure.
Technical Specifications
The Impulse 2 Doors Access Control System includes:
- Multi-computer management capabilities
- Regional interlocking functionality
- Fire alarm linkage for emergency situations
- Dynamic 2D code generation for temporary access
- Cloud platform integration for remote management
- Support for up to 100,000 cardholders and 300,000 event records
- TCP/IP network communication with offline operation capability

Implementation Scenarios
This versatile system adapts to diverse security requirements across different industries and use cases. Here are some key implementation scenarios:
Server Room Protection
Protect critical IT infrastructure with a comprehensive dual-authentication approach:
- First door requires RFID card access with PIN verification
- Second door employs advanced biometric confirmation (fingerprint or facial recognition)
- Complete audit trail of all access attempts with time stamps and user identification
- Integration with environmental monitoring systems for temperature, humidity, and fire detection
- Real-time alerts for unauthorized access attempts or environmental anomalies
Research Laboratory Security
Secure sensitive research areas with sophisticated controls:
- Mantrap configuration to prevent contamination and unauthorized entry
- Multi-tier credential-based access levels for different research zones
- Emergency protocols for hazardous material incidents with automated ventilation control
- Integration with laboratory management systems for seamless operation
- Time-based access restrictions for specific research areas
Executive Suite Protection
Safeguard executive offices with enterprise-grade security measures:
- Reception area with advanced visitor management system and ID verification
- Secondary authentication for inner office access using biometric scanning
- Integration with meeting room scheduling and calendar systems
- Emergency lockdown capabilities with instant notification system
- Video surveillance integration for visual verification of access events
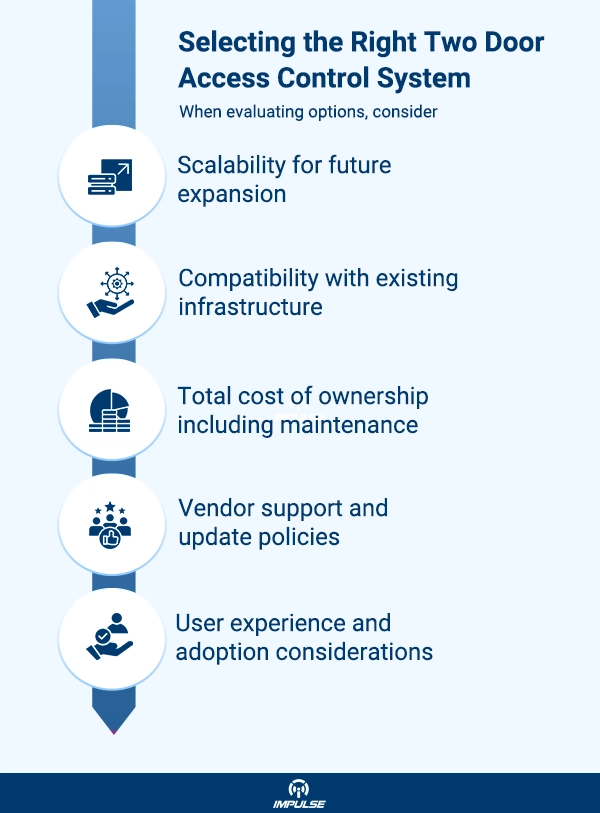
Installation and Configuration Best Practices
Physical Installation Considerations
The physical installation of a two door access control system requires careful planning to ensure optimal security and functionality. Several critical factors must be considered for reliable operation.
Cable routing is essential for both power and network connections, requiring paths that protect against tampering and environmental damage. Backup power solutions through UPS systems or generators are crucial to maintain security during outages.
Reader placement must comply with accessibility standards while maintaining security. External components need weather and tamper protection for reliable operation. Door hardware selection, including electromagnetic or strike locks, should match security requirements and usage patterns.
Network Configuration
A robust network infrastructure is fundamental to modern access control systems. The optimal setup requires several key components for security and performance.
Start with a dedicated VLAN for security systems and implement encrypted communication protocols. Establish comprehensive firewall rules and create redundant network paths for critical installations. Maintain regular security updates and patch management routines.
User Enrollment and Management
Efficient user management balances security requirements with operational efficiency. Organizations need streamlined processes that maintain security while enabling smooth operations.
Implement bulk user import capabilities and create efficient onboarding workflows. Where appropriate, enable self-service credential management. Conduct regular access privilege audits and set up automated expiration for temporary credentials.
Integration Capabilities
Modern access control systems don’t operate in isolation. The Impulse 2 Doors Access Control System features extensive integration capabilities that create a comprehensive security ecosystem. Through its advanced API and standardized protocols, it seamlessly connects with various third-party systems and enterprise applications. Here are the key integration possibilities:
Video Surveillance
- Camera activation upon access events with instant notifications
- Visual verification of credentials through high-resolution video feeds
- Recording of all entry/exit activities with timestamp synchronization
- AI-powered anomaly detection with facial recognition capabilities
- Multi-camera view coordination for comprehensive coverage
Building Management Systems
- HVAC activation based on occupancy patterns and scheduled activities
- Smart lighting control for energy efficiency and security enhancement
- Elevator management for floor-based access restrictions with scheduling options
- Fire alarm and emergency response coordination with automated protocols
- Environmental monitoring and control system integration
Time and Attendance
- Automatic time tracking based on entry/exit with customizable rules
- Contractor hours documentation with detailed reporting features
- Integration with payroll systems for streamlined processing
- Compliance with labor regulations and automatic report generation
- Advanced analytics for workforce management and optimization
Security Considerations for Two Door Access Systems
Risk Assessment
A comprehensive risk assessment is a crucial first step before implementing any access control system. This process involves systematically identifying the critical assets that require protection within your facility, followed by a thorough evaluation of potential threat vectors that could compromise security. Security professionals must carefully determine appropriate security levels for different zones based on the sensitivity of assets and operations in each area. Finally, the assessment should culminate in establishing clear incident response protocols that outline exactly how to handle various security scenarios and breaches.
Tailgating Prevention
Modern access control systems employ sophisticated measures to prevent unauthorized entry through tailgating. These advanced systems utilize a comprehensive approach that includes weight-sensitive flooring technology to detect multiple entrants, directional motion sensors for movement tracking, and AI-powered camera systems that accurately count individuals passing through access points. When violations are detected, the system immediately triggers audio-visual warnings to alert security personnel and deter unauthorized access attempts.
Backup and Redundancy
A robust backup and redundancy strategy is essential for maintaining continuous security operations. The system architecture includes uninterruptible power supplies to ensure functionality during power outages, while offline operation capabilities maintain access control even when network connectivity is compromised. Multiple backup authentication methods provide failsafe access options, and regular system backups with recovery testing ensure data integrity and system reliability in case of equipment failure or other emergencies.
Also Read: 4 Door Access Control System
Conclusion
A robust two door access control system is no longer a luxury but a necessity for organizations serious about physical security. The Impulse 2 Doors Access Control System represents the ideal balance of advanced features, reliability, and integration capabilities that modern security demands.
By implementing a comprehensive access control strategy with the right technology, organizations can protect their assets, ensure regulatory compliance, and provide a secure yet convenient experience for authorized personnel.
Protect your most valuable assets with state-of-the-art access control technology. Impulse CCTV offers complete security solutions tailored to your specific requirements, from initial assessment through installation and ongoing support.