The security landscape is undergoing a revolutionary transformation as Internet of Things (IoT) technology reshapes how we approach access control systems. Traditional lock-and-key mechanisms and standalone card readers are rapidly becoming obsolete, replaced by intelligent, interconnected systems that offer unprecedented levels of security, convenience, and control. This evolution represents more than just a technological upgrade it’s a fundamental shift toward smart security ecosystems that adapt, learn, and respond in real-time.
For businesses, property managers, and security professionals, understanding this transformation is crucial for making informed decisions about their security infrastructure. The integration of IoT into access control systems isn’t just about following trends; it’s about embracing a future where security is proactive, data-driven, and seamlessly integrated into our daily operations.
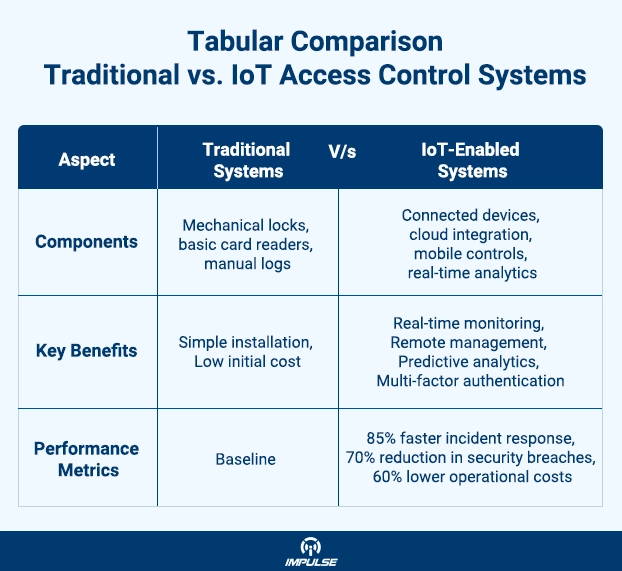
The Limitations of Traditional Access Control
Traditional access control systems have served us well for decades, but they’re increasingly showing their age in our connected world. These conventional systems typically operate in isolation, relying on physical keys, magnetic stripe cards, or basic proximity readers that function independently without any network connectivity or intelligence.
The primary challenges with traditional systems include:
Limited Visibility and Control: Traditional systems provide minimal insight into who accessed what, when, and how. Security managers often discover breaches or unauthorized access long after they’ve occurred, making it difficult to respond effectively or prevent future incidents.
Scalability Issues: Adding new users, changing access permissions, or expanding to multiple locations requires physical intervention at each access point. This manual process is time-consuming, error-prone, and increasingly impractical for growing organizations.
Vulnerability to Physical Compromise: Traditional keys can be duplicated, cards can be cloned, and mechanical locks can be picked. Once compromised, these systems offer little recourse beyond complete replacement.
Lack of Integration: Traditional systems operate in silos, unable to communicate with other security infrastructure like CCTV cameras, alarm systems, or building management platforms. This fragmentation creates security gaps and operational inefficiencies.
The IoT Revolution in Access Control
IoT-enabled access control systems represent a paradigm shift from reactive to proactive security management. These systems leverage connected devices, cloud computing, artificial intelligence, and real-time analytics to create intelligent security ecosystems that can adapt, learn, and respond automatically to changing conditions.
Key IoT Transformations:
Real-Time Connectivity and Monitoring: IoT access control systems maintain constant communication with centralized management platforms, providing instant notifications, live status updates, and comprehensive audit trails. Security managers can monitor and control access across multiple locations from a single dashboard, regardless of their physical location.
Advanced Authentication Methods: Modern IoT systems support multiple authentication factors including biometric recognition, mobile credentials, facial recognition, and dynamic QR codes. The Fixed lens Network Bullet Camera (IMP-LX-BLTF-300-3600) with its built-in microphone and motion detection capabilities exemplifies how surveillance and access control are converging into unified security solutions.
Intelligent Analytics and Automation: IoT systems can analyze access patterns, detect anomalies, and automatically adjust security protocols based on risk assessments. The AI Video Analytics Box (IMP-AiBX-16CH) demonstrates this capability with its support for face recognition, passenger flow analysis, and full target structuring across 16 channels of video analysis.
The Compelling Benefits of IoT Integration
The transformation to IoT-powered access control delivers tangible benefits that directly impact an organization’s security posture, operational efficiency, and bottom line.
Enhanced Security Through Intelligence
IoT systems provide multi-layered security that adapts to threats in real-time. The Varifocal Network Bullet camera (IMP-LX-BLTZ-300-2812) with its 2.7mm to 13.5mm varifocal lens and audio/alarm capabilities creates a comprehensive security perimeter that can zoom in on suspicious activities while maintaining broad area coverage.
Predictive Security Analytics: By analyzing access patterns, visitor behavior, and environmental factors, IoT systems can predict and prevent security incidents before they occur. This proactive approach represents a fundamental shift from reactive security measures.
Seamless Integration: Modern IoT platforms integrate video surveillance, access control, and building automation into unified systems. The TCP/IP Two Doors Access Control System (IMP-ACS-2DRACB) exemplifies this integration with its multi-computer management, regional interlocking, and fire linkage capabilities.
Operational Efficiency and Cost Reduction
Remote Management: Security managers can control access permissions, monitor system status, and respond to incidents from anywhere with internet connectivity. This capability is particularly valuable for organizations with multiple locations or remote facilities.
Automated Compliance: IoT systems automatically generate compliance reports, maintain detailed audit trails, and ensure regulatory requirements are met without manual intervention.
Scalable Architecture: The cloud-based infrastructure of IoT systems allows for easy expansion and modification without significant hardware investments. The TCP/IP Four Doors Access Control System (IMP-ACS-4DRACB) demonstrates this scalability with its advanced management features and cloud platform integration.
User Experience Enhancement
Mobile-First Approach: Modern IoT access control systems prioritize mobile experiences, allowing users to gain access through smartphone apps, eliminating the need for physical cards or keys.
Personalized Access: Systems can provide customized access experiences based on user roles, time of day, and specific requirements, creating a more intuitive and secure environment.
Technical Advantages
Edge Computing: Modern IoT access control systems incorporate edge analytics for faster decision-making and reduced dependence on internet connectivity. This ensures security operations continue even during network disruptions.
Interoperability: ONVIF compliance and standardized protocols ensure compatibility with existing security infrastructure, protecting previous investments while enabling future expansion.
Advanced Analytics: Machine learning algorithms continuously improve system performance by learning from user behavior patterns and environmental conditions.
Implementing IoT Access Control Solutions
The transition to IoT-enabled access control requires careful planning and strategic implementation. Organizations must consider their current infrastructure, security requirements, and future growth plans when designing their IoT security ecosystem.
Implementation Strategy
Assessment and Planning: Begin with a comprehensive security audit to identify vulnerabilities in existing systems and define requirements for the new IoT infrastructure. Consider factors like user count, access points, integration needs, and compliance requirements.
Phased Deployment: Implement IoT access control in phases, starting with high-priority areas and gradually expanding throughout the facility. This approach minimizes disruption while allowing for system optimization and user training.
Integration Considerations: Ensure new IoT systems can integrate with existing security cameras, alarm systems, and building management platforms. The combination of access control boards with intelligent video analytics creates a comprehensive security solution that maximizes the value of each component.

Technology Selection Criteria
Scalability: Choose systems that can grow with your organization’s needs without requiring complete replacement.
Security Standards: Ensure all IoT devices comply with industry security standards and support encryption, secure authentication, and regular firmware updates.
User Experience: Prioritize solutions that enhance rather than complicate the user experience, encouraging adoption and compliance.
Future-Proofing Your Investment
Cloud-Ready Architecture: Select systems that leverage cloud computing for management, analytics, and updates, ensuring access to the latest features and security enhancements.
AI Integration: Choose platforms that support artificial intelligence and machine learning capabilities for predictive analytics and automated responses.
Standards Compliance: Ensure compatibility with emerging standards and protocols to maintain interoperability as technology evolves.
Conclusion
The transformation of traditional access control systems through IoT technology represents more than a technological upgrade it’s a fundamental reimagining of how we approach security in the modern world. Organizations that embrace this evolution gain access to intelligent security ecosystems that provide unprecedented visibility, control, and protection.
The benefits extend far beyond enhanced security to include improved operational efficiency, reduced costs, and better user experiences. As cyber threats continue to evolve and security requirements become more complex, IoT-enabled access control systems provide the flexibility, intelligence, and scalability needed to stay ahead of emerging challenges.
The future of access control is not just connected it’s intelligent, adaptive, and seamlessly integrated into our daily lives. Organizations that invest in IoT access control solutions today are not just protecting their assets; they’re building the foundation for tomorrow’s smart security infrastructure.
Don’t let outdated access control systems leave your organization vulnerable. Discover how Impulse’s comprehensive IoT security solutions can revolutionize your access control capabilities.


