In today’s security-conscious environment, access control systems have evolved from simple lock-and-key mechanisms to sophisticated digital solutions that balance security, convenience, and operational efficiency. Choosing between card-based access control and biometric access control represents one of the most critical decisions organizations face when designing their physical security infrastructure.
This comprehensive guide examines both technologies from a technical perspective, analyzing their architecture, deployment considerations, integration capabilities, and real-world applications. Whether you’re securing a corporate office, manufacturing facility, healthcare institution, or data center, understanding the nuances of each system will help you make an informed decision that aligns with your security requirements, budget constraints, and long-term operational goals.

Understanding Card-Based Access Control Systems
Technical Architecture and Operation
Card access control systems utilize RFID (Radio-Frequency Identification) technology to grant or deny entry based on encoded credentials stored on physical access cards. The system comprises four primary components: access cards, card readers, control panels, and management software.
When an authorized user presents their credential, the card reader captures the unique identifier through electromagnetic induction. Modern systems like the TCP/IP Two Doors Access Control System process this information through TCP/IP network protocols, enabling real-time communication with centralized management servers. This networked architecture supports advanced features including multi-computer management, regional interlocking, and fire linkage protocols.
Card Technology Variations
The MIFARE 13.56MHz IC Card exemplifies modern contactless card technology, operating at the 13.56MHz frequency band. These cards employ encrypted initialization and anti-replay protection, preventing unauthorized duplication through sophisticated cryptographic algorithms. Each card contains a unique serial number burned into the chip during manufacturing, providing an immutable identifier that cannot be cloned through conventional means.
Key technical specifications of MIFARE IC cards include:
- Data retention: Minimum 10 years without power
- Read/write cycles: Up to 100,000 operations
- Communication distance: 2-10 cm (optimized for security)
- Memory architecture: Hierarchical key structure supporting multi-application deployment
- Operating temperature: -20°C to +50°C for industrial environments
For organizations requiring enhanced versatility, the QR Code Card Reader represents an evolution in credential recognition technology. This device integrates advanced RFID circuitry with optical image recognition, supporting multiple credential formats including QR codes, MIFARE cards, NFC-enabled smartphones, and legacy card technologies. This multi-modal approach provides flexibility during system migrations and supports bring-your-own-device (BYOD) security policies.
Infrastructure Requirements
Implementing card-based access control requires careful consideration of network infrastructure and power distribution. The TCP/IP Four Doors Access Control System demonstrates the scalability achievable through modern network architecture, managing four independent access points from a single control board while maintaining individual door policies and monitoring capabilities.
Network topology considerations include:
- Bandwidth allocation: Minimum 10 Mbps per control panel for real-time event logging
- Power over Ethernet (PoE): Support for IEEE 802.3af/at standards
- Failover protocols: Local authentication caching during network interruptions
- Encryption standards: TLS 1.3 for data transmission security
- Cloud platform integration: API-based connectivity for centralized management
Physical installation requirements extend beyond electronic components. The Stainless Steel Door Exit Push Button exemplifies the mechanical durability required for high-traffic environments. Manufactured from corrosion-resistant stainless steel, these switches withstand millions of actuation cycles while maintaining electrical contact integrity.
Understanding Biometric Access Control Systems
Biometric Modalities and Selection Criteria
Biometric access control eliminates the dependency on physical credentials by authenticating individuals based on unique physiological characteristics. The most commonly deployed modalities include fingerprint recognition, facial recognition, iris scanning, and palm vein authentication. Each technology presents distinct advantages regarding accuracy, speed, user acceptance, and environmental resilience.
Fingerprint recognition systems operate through one of three sensor technologies:
- Optical sensors: Capture digital images of fingerprint ridges using LED arrays and CMOS sensors. These provide excellent resolution (500+ DPI) but can be affected by surface contamination and lighting conditions.
- Capacitive sensors: Measure electrical conductivity differences between ridges and valleys, creating a three-dimensional fingerprint map. These sensors resist spoofing attempts using photographs or molds.
- Thermal sensors: Detect temperature differentials across fingerprint topography, providing living tissue verification that prevents presentation attacks.
Facial recognition systems have advanced significantly through deep learning algorithms and neural network architectures. Modern implementations achieve authentication in varying lighting conditions, can compensate for facial hair or cosmetic changes, and perform liveness detection to prevent spoofing through photographs or videos. These systems typically require 3D structured light or time-of-flight sensors to build accurate facial geometry models.
Performance Metrics and Accuracy Standards
Evaluating biometric system performance requires understanding industry-standard metrics that quantify reliability and security:
False Acceptance Rate (FAR) measures the probability that the system incorrectly authenticates an unauthorized user. High-security applications target FAR values below 0.001% (1 in 100,000), while standard commercial deployments operate at 0.01% (1 in 10,000). Government facilities and data centers often specify FAR thresholds of 0.0001% or lower.
False Rejection Rate (FRR) quantifies how often legitimate users are denied access. While security-focused organizations tolerate higher FRR to minimize breach risks, user experience considerations typically constrain FRR to 1-3% in commercial environments. High FRR causes operational friction, leading to user frustration and reduced system acceptance.

Equal Error Rate (EER) represents the point where FAR equals FRR, providing a single metric for comparing biometric algorithm performance. Enterprise-grade systems typically achieve EER values between 0.01% and 0.1%, with iris recognition systems offering the lowest EER among mainstream biometric modalities.
Enrollment Process and Template Management
Successful biometric system deployment begins with comprehensive enrollment procedures. During enrollment, the system captures multiple samples of the biometric characteristic, extracts distinctive features, and generates a mathematical biometric template stored in the access control database.
Template generation involves sophisticated signal processing:
- Image acquisition: Multiple captures ensure consistent quality despite variations in presentation angle, pressure, or environmental conditions.
- Feature extraction: Algorithms identify minutiae points (for fingerprints), facial landmarks, or iris crypts, converting biological characteristics into numerical vectors.
- Template creation: Extracted features are encoded into a compact mathematical representation, typically 256-512 bytes, enabling rapid database searching.
- Quality assessment: Each template receives a quality score; substandard enrollments are rejected to prevent future authentication failures.
Modern systems employ distributed template storage architectures, maintaining encrypted templates across multiple database instances with automatic synchronization. This approach enhances system resilience while maintaining sub-second authentication response times even with databases containing 100,000+ enrolled users.
Comparative Analysis: Security Considerations
Credential Security and Vulnerability Assessment
Card-based systems present specific vulnerability vectors that security architects must address. Physical cards can be lost, stolen, or transferred to unauthorized individuals, creating credential sharing risks. However, modern implementations mitigate these concerns through multi-factor authentication protocols combining card possession with PIN codes or biometric verification.
The ID Card Writer enables on-site credential provisioning with USB connectivity and microcomputer control, eliminating dependencies on external vendors for card encoding. This capability reduces credential issuance timeframes from days to minutes while maintaining cryptographic security through proper key management protocols.
Anti-cloning technologies embedded in modern access cards include:
- Challenge-response authentication: The reader sends random challenges that the card must answer using secret keys, preventing replay attacks.
- Diversified keys: Each card uses unique cryptographic keys derived from master secrets, ensuring that compromising one card doesn’t expose the entire system.
- Rolling codes: Credentials change after each successful authentication, similar to garage door opener security.
Biometric systems offer inherent advantages against credential sharing since physiological characteristics cannot be easily transferred. However, they introduce different security considerations:
Presentation attack detection (PAD) systems must defend against spoofing attempts using photographs, silicone fingerprints, or contact lenses with printed iris patterns. Advanced sensors employ liveness detection through:
- Pulse oximetry: Detecting blood flow beneath the skin surface
- Thermal analysis: Verifying body temperature consistency
- Texture analysis: Identifying living tissue characteristics through microscopic examination
- 3D depth mapping: Ensuring physical presence rather than flat presentations
Template security requires encryption both at rest and in transit. Biometric templates represent sensitive personal data under regulations like GDPR, necessitating secure enclave storage, homomorphic encryption for matching operations, and comprehensive audit trails documenting template access.
Audit Capabilities and Compliance Requirements
Both systems provide comprehensive audit logging, but implementation details differ significantly. Card-based systems generate event records containing timestamps, user identifiers, door locations, and access decisions. These logs integrate seamlessly with Security Information and Event Management (SIEM) platforms for real-time threat detection.
Biometric access logs must balance forensic value with privacy protection. While authentication timestamps and locations are recorded, the actual biometric data should never appear in logs. Advanced systems implement privacy-preserving audit trails that enable compliance verification without exposing sensitive biometric information.
Regulatory frameworks impose specific requirements:
- HIPAA (Healthcare): 24/7 audit trail availability, automatic backup procedures, and tamper-evident logging
- PCI DSS (Payment Card Industry): Quarterly access reviews, automated deprovisioning procedures, and segregation of duties enforcement
- GDPR (European Union): Right to erasure of biometric templates, explicit consent documentation, and data processing agreements
Operational Considerations and Use Case Analysis
Throughput and User Experience
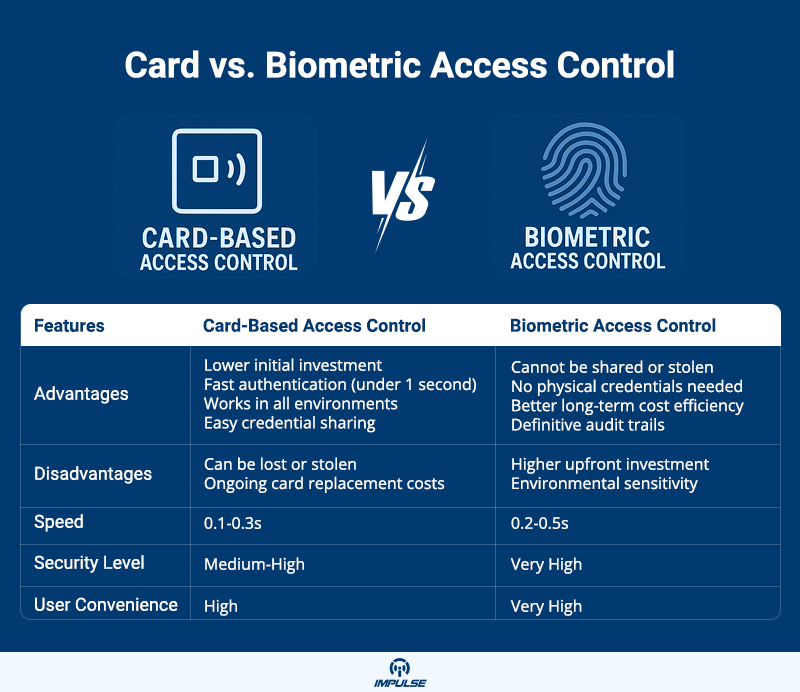
Authentication speed directly impacts user satisfaction and facility throughput. Card-based systems typically process authentications in 0.1-0.3 seconds, enabling smooth traffic flow even during peak periods like shift changes. The instantaneous nature of card presentation creates minimal user friction.
Biometric authentication requires 0.2-0.5 seconds for fingerprint systems and 0.5-2.0 seconds for facial recognition, depending on database size and algorithm complexity. While slightly slower than cards, biometric systems eliminate the fumbling delay associated with retrieving cards from wallets or bags. For facilities processing thousands of daily authentications, this user experience consideration proves significant.
Environmental resilience varies substantially between modalities:
Card readers function reliably across extreme temperature ranges (-40°C to +70°C) and are unaffected by user-specific factors like injuries, illness, or physiological changes. However, proximity cards can be damaged by electromagnetic interference or physical trauma.
Biometric sensors face environmental challenges including:
- Fingerprint sensors: Degraded performance with wet, dirty, or calloused fingers common in manufacturing or outdoor environments
- Facial recognition: Reduced accuracy under poor lighting, dramatic shadowing, or when users wear protective equipment like respirators
- Iris scanners: Excellent environmental resilience but require specific positioning and user cooperation, slowing throughput
Scalability and System Integration
Modern access control infrastructure must integrate with broader security ecosystems including video surveillance, intrusion detection, visitor management, and building automation systems. Both card and biometric technologies support these integrations through standardized protocols, but implementation complexity differs.
The TCP/IP architecture in systems like the Two Doors Access Control System (IMP-ACS-2DRACB) and Four Doors Access Control System (IMP-ACS-4DRACB) enables cloud platform integration and distributed management, supporting geographically dispersed facilities through centralized administration. These systems implement regional interlocking protocols that coordinate multiple access points, preventing tailgating and enforcing occupancy limits.
Dynamic 2D code support in modern access control boards accommodates temporary credentials generated through mobile applications, enabling visitor access without physical credential issuance. This capability bridges traditional card-based infrastructure with contemporary mobile-first approaches.
Fire linkage protocols represent critical safety integrations, automatically unlocking designated egress doors when fire alarm systems activate. Both card and biometric systems must comply with life safety codes ensuring reliable fail-safe operation during emergencies.
Maintenance Requirements and Lifecycle Management
Card system maintenance primarily involves reader cleaning, card reader calibration, and credential lifecycle management. Organizations must implement processes for:
- Immediate deactivation of lost or stolen cards
- Bulk deprovisioning during employee terminations or contractor completions
- Periodic access rights reviews ensuring privilege alignment with job roles
- Card stock management and replacement provisioning
The ID Card Writer streamlines credential management through fast reading speeds and USB connectivity, enabling decentralized card provisioning without specialized technical expertise.
Biometric system maintenance emphasizes sensor hygiene, template database optimization, and algorithm performance monitoring. Fingerprint sensors require regular cleaning to maintain optical clarity, while facial recognition cameras need lens maintenance and lighting verification.
Database performance optimization becomes critical as enrollment counts increase. Systems must implement:
- Indexed searching algorithms maintaining sub-second response times with 100,000+ templates
- Distributed database architectures balancing authentication loads across multiple servers
- Template quality audits identifying degraded enrollments requiring re-registration
- Algorithm updates incorporating improved feature extraction and matching techniques
Implementation Decision Framework
Selecting the Appropriate Technology
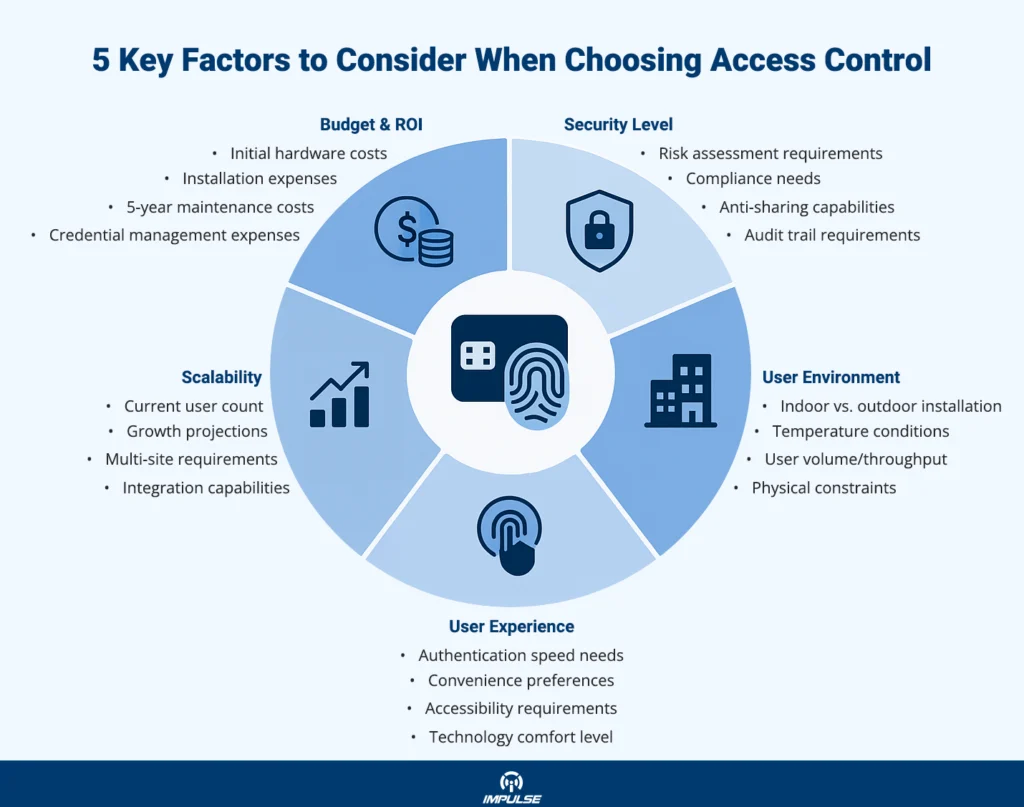
Choosing between card-based and biometric access control requires evaluating multiple factors specific to your organization’s operational context, security requirements, and budget constraints.
Card systems prove optimal when:
- Environmental conditions preclude reliable biometric capture (extreme temperatures, high particulate contamination, or outdoor installations)
- User populations include individuals with biometric capture challenges (manual laborers with worn fingerprints, visually impaired individuals)
- Privacy concerns limit biometric data collection due to cultural, legal, or organizational policies
- Budget constraints necessitate lower initial capital investment
- Credential sharing requirements exist, such as shared equipment access in laboratories or manufacturing
- Rapid throughput demands immediate authentication with minimal user interaction
Biometric systems excel when:
- Security requirements mandate non-transferable credentials preventing unauthorized sharing
- Audit trails must definitively attribute access events to specific individuals
- Credential management overhead associated with card issuance, replacement, and deactivation becomes prohibitive
- User populations experience frequent credential loss or theft
- Hygiene protocols discourage shared touchpoints like card readers or PIN pads
- Long-term cost optimization justifies higher initial investment through eliminated credential costs
Hybrid approaches combining both technologies offer maximum flexibility, deploying biometric authentication at high-security perimeters while using cards for general office areas. This layered security architecture optimizes cost-effectiveness while maintaining stringent controls where required.
Integration with Existing Infrastructure
Successful access control system deployment requires careful evaluation of existing physical security infrastructure, network architecture, and management processes. Organizations must assess:
Network readiness: Modern TCP/IP access control systems require reliable network connectivity with appropriate bandwidth, redundancy, and security. Legacy installations may necessitate network infrastructure upgrades to support distributed control panels and centralized management platforms.
Power distribution: Access control components require reliable power with battery backup ensuring operation during outages. Power over Ethernet (PoE) simplifies installation but requires switches supporting appropriate IEEE standards.
Physical hardware compatibility: Door hardware, electric strikes, magnetic locks, and exit devices must integrate properly with access control systems. The Stainless Steel Door Exit Push Button demonstrates the importance of selecting durable, reliable mechanical components compatible with electronic access control logic.
Software ecosystems: Access control management software must integrate with HR databases for automated provisioning, SIEM platforms for security monitoring, and video management systems for correlated event investigation.
Future Trends and Emerging Technologies
The access control industry continues evolving rapidly, driven by advances in artificial intelligence, mobile computing, and cloud architectures. Emerging trends reshaping the landscape include:
Mobile credentials utilizing NFC and Bluetooth Low Energy (BLE) protocols enable smartphones to function as access credentials. The QR Code Card Reader exemplifies this trend through multi-modal credential support, accommodating both traditional cards and mobile-generated codes.
Artificial intelligence enhances biometric accuracy through neural network architectures trained on millions of samples, improving performance in challenging conditions and detecting sophisticated presentation attacks. AI-powered analytics also identify anomalous access patterns indicating potential security incidents.
Cloud-native architectures eliminate on-premise management servers, enabling global administration through web browsers while maintaining local authentication capability during internet outages. These platforms offer automatic updates, elastic scaling, and comprehensive API integrations.
Touchless authentication technologies gained prominence during the COVID-19 pandemic, driving adoption of facial recognition, iris scanning, and mobile credential systems minimizing physical touchpoints. This trend continues as organizations prioritize hygiene and user convenience.
Conclusion
Choosing between card-based and biometric access control represents a strategic decision with long-term implications for security posture, operational efficiency, and total cost of ownership. Both technologies offer viable solutions, with optimal selection depending on your organization’s specific requirements, environmental conditions, regulatory obligations, and budget constraints.
Card access control systems like the TCP/IP Two Doors Access Control System and TCP/IP Four Doors Access Control System provide proven reliability, environmental resilience, and lower initial investment. The use of advanced credentials such as the MIFARE 13.56MHz IC Card ensures strong cryptographic security, while devices like the QR Code Card Reader flexible multi-modal authentication strategies.
Biometric access control delivers unparalleled security through non-transferable credentials, eliminates ongoing card management overhead, and provides definitive audit trails. While requiring higher initial investment, biometric systems often prove more cost-effective over extended operational periods, particularly for organizations with large user populations or high credential replacement rates.
Hybrid implementations leveraging both technologies offer optimal solutions for many organizations, deploying biometric authentication at critical control points while using cards for general access. This approach balances security, convenience, and cost-effectiveness while providing flexibility for future technology adoption.
Regardless of which technology you select, successful implementation requires careful planning, comprehensive user training, robust integration with existing security infrastructure, and ongoing maintenance ensuring reliable long-term operation.
At Impulse, we design and implement access control solutions tailored to your security needs. Our certified professionals provide security assessments and technology selection guidance, professional installation and system integration, plus ongoing support and maintenance. Contact Impulse today to design a security solution that protects your people, assets, and operations.


