In an era where security breaches and unauthorized access pose significant threats to critical infrastructure, government facilities, data centers, and corporate headquarters, implementing robust access control systems has become non-negotiable. High-security locations demand more than traditional lock-and-key solutions—they require intelligent, multi-layered physical security systems that combine cutting-edge technology with operational efficiency.

Introduction
Access control systems serve as the first line of defense in protecting sensitive areas, valuable assets, and personnel in high-security environments. Unlike conventional security measures, modern TCP/IP access control systems leverage networked infrastructure, biometric authentication, multi-factor verification, and cloud-based management platforms to deliver comprehensive security solutions.
This article explores the technical architecture, essential components, and strategic implementation of enterprise-level access control systems specifically designed for facilities requiring maximum security protocols. Whether you’re securing a financial institution, healthcare facility, research laboratory, or government building, understanding the technical specifications and capabilities of modern access control infrastructure is crucial for making informed security investments.
Understanding High-Security Access Control Architecture
What Makes an Access Control System “High-Security”?
High-security access control systems differ fundamentally from standard commercial solutions through their enhanced features and robust technical specifications:
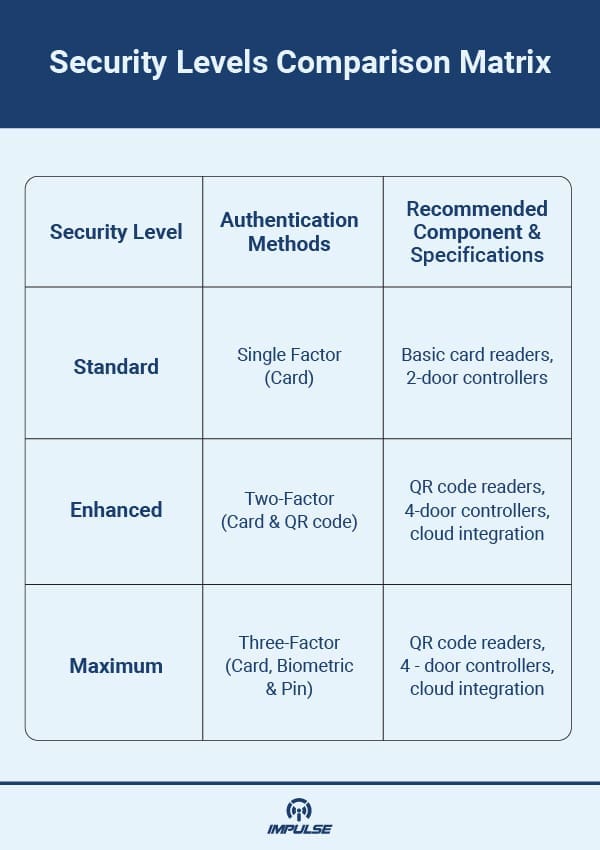
Multi-Layer Authentication Protocols: High-security environments typically implement two-factor or three-factor authentication combining something you have (credential cards), something you know (PIN codes), and something you are (biometric data).
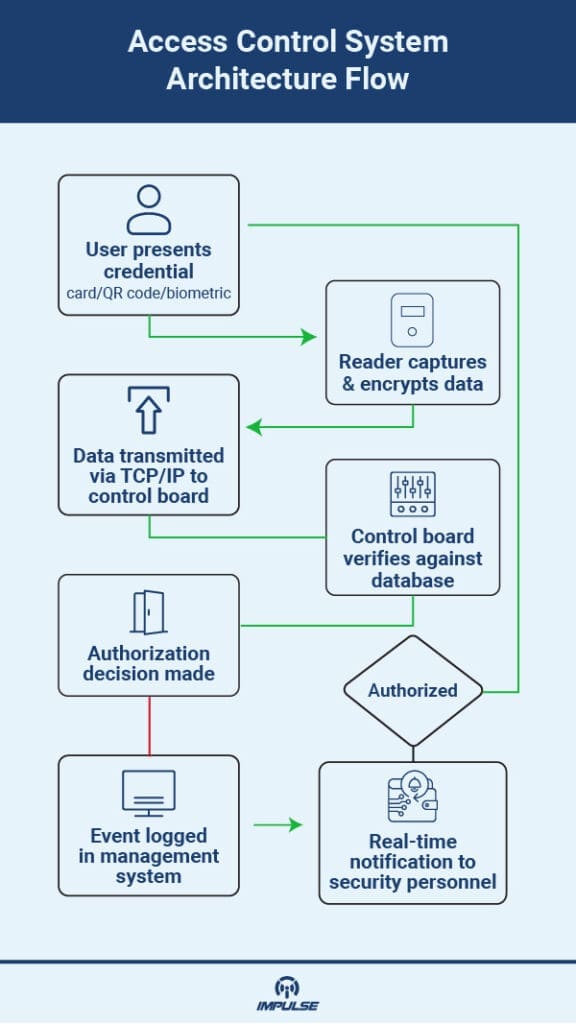
Network-Based Control Infrastructure: Modern systems utilize TCP/IP communication protocols enabling centralized management across multiple doors, buildings, and even geographic locations. The TCP/IP Two Doors Access Control System exemplifies this architecture, providing enhanced features including multi-computer management, regional interlocking, and fire linkage capabilities.
Scalability and Expansion Capabilities: Enterprise-grade solutions must accommodate growth. For larger facilities, the TCP/IP Four Doors Access Control System offers expanded capacity while maintaining advanced features like dynamic 2D code authentication and cloud platform integration.
Real-Time Monitoring and Logging: Comprehensive audit trails and real-time monitoring capabilities ensure complete visibility into access events, anomalies, and security incidents.
Core Components of High-Security Access Control Systems
1. Intelligent Control Panels and Boards
The control board functions as the system’s central processing unit, managing authentication requests, door operations, and system communications. Modern access control boards incorporate:
- Embedded processors for local decision-making
- Encrypted communication channels preventing data interception
- Backup power systems ensuring operation during power failures
- Regional interlocking capabilities preventing simultaneous door openings in secure zones
2. Credential Readers and Authentication Devices
Credential authentication represents the critical interface between users and the security system. High-security implementations typically deploy:
Advanced RFID Card Readers: The MIFARE 13.56MHz IC Card provides secure, contactless data transmission with encrypted initialization, long-term data retention, and unique serial numbering. This technology supports multi-application functionality with key hierarchy and anti-replay protection, essential for preventing credential cloning attacks.
QR Code and Multi-Format Readers: Modern facilities increasingly adopt QR Code Card Readers featuring advanced RFID circuitry and image recognition capabilities. These readers support QR codes, MIFARE, NFC, and multiple card formats while maintaining high sensitivity, low power consumption, and excellent performance characteristics.
Dynamic Credential Systems: Integration of dynamic 2D codes provides time-sensitive credentials that automatically expire, significantly reducing risks associated with stolen or shared credentials.
Essential Peripheral Devices for Complete Security
Exit Controls and Emergency Systems
Exit Push Button Controls: The Switch Panel Door Exit Push Button manufactured from durable stainless steel plate construction provides reliable manual override capabilities. These devices are critical for:
- Emergency egress during fire alarms or evacuations
- ADA compliance requirements
- Integration with fire linkage systems for automatic unlocking
- Tamper-resistant installations in high-traffic areas
Credential Programming and Management
Card Writers and Programmers: The ID Card Writer features fast reading speeds, high-quality microcomputer control, and USB compatibility for efficient data transmission without driver installation requirements. This streamlines credential provisioning processes essential in facilities with high employee turnover or frequent visitor access.

Advanced Features for High-Security Applications
Multi-Computer Management and Centralization
Enterprise environments with distributed security operations benefit significantly from multi-computer management capabilities. This architecture enables:
- Centralized credential management across entire organizations
- Role-based access control (RBAC) with granular permission settings
- Unified monitoring dashboards providing comprehensive security visualization
- Automated reporting for compliance documentation
Regional Interlocking and Anti-Passback
Regional interlocking prevents simultaneous access to multiple doors within defined security zones, essential for:
- Mantrap configurations in data centers
- Secure corridors in government facilities
- Vault areas in financial institutions
- Cleanroom access in pharmaceutical manufacturing
Anti-passback protocols ensure credentials cannot be shared or used by multiple individuals simultaneously, maintaining strict accountability in high-security environments.
Fire Linkage and Emergency Response Integration
Modern access control systems must integrate seamlessly with fire alarm systems and emergency response protocols. Fire linkage capabilities automatically:
- Unlock designated egress doors upon alarm activation
- Secure sensitive areas while facilitating safe evacuation
- Provide firefighters with override capabilities
- Generate detailed evacuation reports for post-incident analysis
Cloud Platform Integration and Remote Management
The evolution toward cloud-based access control represents a paradigm shift in security management. Cloud platform integration delivers:
Scalability: Easily add locations, doors, and users without hardware infrastructure investments
Remote Management: Configure permissions, monitor events, and respond to security incidents from any internet-connected device
Automatic Updates: System firmware and software updates deploy automatically, ensuring security protocols remain current
Data Analytics: Advanced reporting capabilities identify usage patterns, potential vulnerabilities, and optimization opportunities
Disaster Recovery: Cloud-based credential databases and configuration backups ensure business continuity
Implementation Considerations for High-Security Locations
Site Assessment and Security Analysis
Successful implementation begins with comprehensive security risk assessment:
- Identify critical assets and vulnerabilities
- Map personnel flow and access requirements
- Determine authentication level requirements for each zone
- Evaluate existing infrastructure compatibility
Network Infrastructure Requirements
TCP/IP access control systems demand robust network infrastructure:
- Dedicated VLANs for security system traffic
- Power over Ethernet (PoE) capabilities for simplified installation
- Network redundancy ensuring system availability
- Cybersecurity protocols including firewalls and encryption
Compliance and Regulatory Requirements
High-security facilities must address various compliance frameworks:
- HIPAA requirements for healthcare facilities
- PCI DSS standards for financial environments
- FISMA compliance for government installations
- SOC 2 certification for data centers
Future-Proofing Your Access Control Investment
Emerging Technologies and Trends
The access control landscape continues evolving with emerging technologies:
Artificial Intelligence Integration: AI-powered systems detect anomalies, predict security incidents, and automate response protocols
Mobile Credentials: Smartphone-based access using Bluetooth Low Energy (BLE) and NFC technology
Biometric Advancement: Enhanced facial recognition, iris scanning, and multi-modal biometric systems
IoT Integration: Connecting access control with building automation systems, lighting, HVAC, and energy management
Maintenance and System Lifecycle Management
Protecting your investment requires ongoing maintenance:
- Regular firmware updates addressing security vulnerabilities
- Periodic testing of emergency override and fire linkage functions
- Credential audit programs removing inactive users
- Hardware inspection ensuring reader and lock functionality
Conclusion
Implementing access control systems in high-security locations demands careful consideration of technical capabilities, operational requirements, and future expansion needs. Modern solutions combining TCP/IP network architecture, multi-factor authentication, cloud-based management, and emergency integration provide the comprehensive security framework essential for protecting critical assets and personnel.
The Impulse CCTV product portfolio offers scalable solutions ranging from two-door to four-door control systems, advanced QR code and MIFARE card readers, durable exit control devices, and efficient credential programming tools. Each component integrates seamlessly within comprehensive security architectures designed to meet the demanding requirements of high-security environments.
When selecting an access control system, prioritize solutions offering robust authentication methods, comprehensive integration capabilities, scalable architecture, and proven reliability in mission-critical applications. The investment in quality infrastructure pays dividends through enhanced security, operational efficiency, and long-term system sustainability.
Get expert protection with Impulse’s advanced access control. Our team will design a custom security solution using TCP/IP technology, multi-factor authentication, and cloud integration. Secure your most valuable assets with our enterprise-grade systems.


