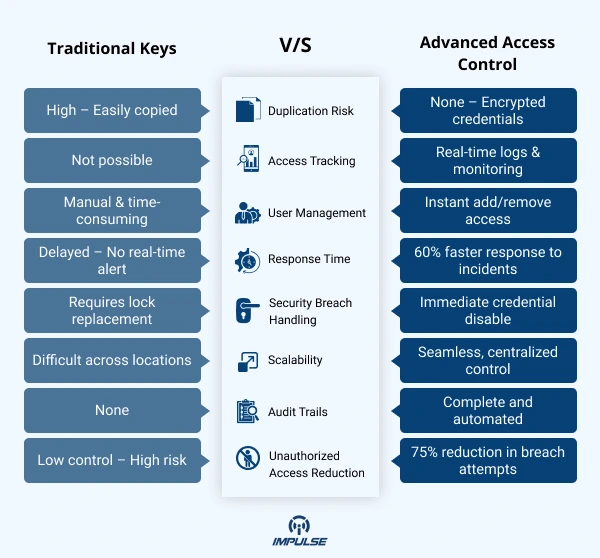
Security breaches cost businesses an average of $4.45 million per incident, with unauthorized physical access being a primary vulnerability point. Traditional lock-and-key systems no longer provide adequate protection for modern commercial environments, where sensitive data, valuable assets, and employee safety require sophisticated security measures.
Advanced access control systems represent the evolution of business security, offering comprehensive solutions that go beyond simple entry management. These intelligent systems provide multi-layered protection, real-time monitoring, and seamless integration with existing security infrastructure.
The Hidden Vulnerabilities in Traditional Security
The Critical Security Gap
Most businesses operate under a false sense of security with conventional locking mechanisms. Physical keys can be duplicated, lost, or stolen without immediate detection. Employee turnover creates ongoing security risks when former staff retain access credentials. Visitor management becomes a logistical nightmare without proper tracking systems.
Commercial door access systems address these fundamental weaknesses by implementing digital authentication, audit trails, and instant access modification capabilities. Unlike traditional keys, digital credentials can be immediately deactivated, tracked in real-time, and configured with specific time and location restrictions.
Emerging Security Threats
Modern businesses face increasingly sophisticated security challenges. Corporate espionage, data theft, and insider threats require advanced countermeasures that traditional security cannot provide. Business security systems must evolve to address these complex threat vectors while maintaining operational efficiency.

Understanding Advanced Access Control Technology
Core Components of Modern Access Control
Advanced access control systems integrate multiple technologies to create comprehensive security solutions. The foundation includes intelligent control boards, authentication devices, electromagnetic locks, and centralized management software.
2 Door Access Control Systems like the TCP/IP Two Doors Access Control System (IMP-ACS-2DRACB) provide enhanced multi-computer management with regional interlocking capabilities. These systems support fire linkage protocols, ensuring emergency egress compliance while maintaining security integrity. Dynamic 2D code integration enables flexible authentication methods, while cloud platform connectivity allows remote monitoring and management.
4 Door Access Control Systems such as the TCP/IP Four Doors Access Control System (IMP-ACS-4DRACB) extend these capabilities across larger facilities. Multi-door coordination ensures synchronized security protocols throughout expansive commercial spaces. Advanced features include zone-based access control, time-scheduled permissions, and integrated alarm systems.
Authentication Technologies
Modern business access control systems support multiple authentication methods:
- RFID Technology: The Metal RFID Card Reader MIFARE (IMP-ACS-MRFCR) utilizes 13.56MHz frequency with encryption algorithms, providing high sensitivity and minimal error rates. Wiegand output compatibility ensures seamless integration with existing systems.
- Card Programming: The ID Card Writer (IMP-ACS-CW) enables rapid credential creation with high-quality microcomputer control and USB compatibility, eliminating driver installation requirements.
- Biometric Integration: Advanced systems support fingerprint, facial recognition, and multi-factor authentication for maximum security.
Infrastructure Components
Professional installation requires robust supporting infrastructure:
- Electromagnetic Locks: The 280KG Double Door Electromagnetic Lock (IMP-ACS-DDMLCK) features epoxy-less design with superior finish quality and easy installation protocols.
- Access Control Housing: The Access Control Housing with Power Supply Box (IMP-ACS-PWSH) includes built-in power supply and lock facilities, designed to support control boards, EM locks, and readers in integrated configurations.
- Exit Controls: The Switch Panel Door Exit Push Button Access Control (IMP-ACS-MEXPBTN) provides durable, weather-resistant egress control.
Compelling Benefits of Implementation
Operational Efficiency Gains
Security systems for businesses provide immediate operational improvements beyond basic protection. Automated access logging eliminates manual visitor management processes. Real-time monitoring reduces security personnel requirements. Centralized control enables instant system-wide modifications without physical key distribution.
Benefits of access control systems extend to workforce management through detailed attendance tracking and zone-based productivity monitoring. Integration with HR systems streamlines employee onboarding and offboarding processes. Automated compliance reporting satisfies regulatory requirements without additional administrative overhead.
Financial Impact Analysis
ROI calculations demonstrate compelling financial benefits:
- Reduced Security Costs: Elimination of lock rekeying expenses, reduced security guard requirements, and minimized theft losses
- Insurance Benefits: Many insurers offer premium reductions for businesses with certified access control systems
- Productivity Gains: Streamlined entry processes, reduced administrative overhead, and enhanced operational visibility
Risk Mitigation Capabilities
Advanced access control systems provide comprehensive risk management through multiple security layers. Audit trails create forensic evidence for incident investigation. Real-time alerts enable immediate response to security breaches. Integration with surveillance systems provides complete security ecosystem management.

Scalability and Future-Proofing
Modern systems accommodate business growth through modular expansion capabilities. Cloud-based management enables multi-location coordination. Regular software updates ensure continued protection against emerging threats. Integration APIs support future technology adoption.
Implementation Strategy for Your Business
Assessment and Planning Phase
Why businesses need access control becomes clear through comprehensive security audits. Professional assessment identifies vulnerability points, traffic patterns, and integration requirements. Customized solutions address specific operational needs while providing scalable expansion capabilities.
Technical specifications must align with facility requirements:
- Door quantity and configuration
- User capacity and authentication methods
- Integration with existing security systems
- Compliance requirements and emergency protocols
Professional Installation Process
Secure office entry solutions require expert implementation to ensure optimal performance. Professional installation includes:
- Infrastructure Preparation: Power supply configuration, network connectivity, and hardware mounting
- System Configuration: Software setup, user database creation, and access parameter definition
- Integration Testing: Compatibility verification with existing systems and emergency protocols
- Staff Training: Administrative interface instruction and operational procedure development
Ongoing Management and Support
Effective door access control systems require continuous optimization through regular maintenance, software updates, and performance monitoring. Professional support ensures system reliability and maximizes security benefits.
Technical Specifications
TCP/IP Two Doors Access Control System (IMP-ACS-2DRACB) Features:
- Multi-computer management capability for seamless control across multiple workstations and locations
- Regional interlocking functionality ensures coordinated access control between different building zones
- Fire linkage integration provides automatic emergency response and evacuation support
- Dynamic 2D code support enables secure, temporary access through mobile devices
- Cloud platform connectivity for remote management and real-time monitoring
TCP/IP Four Doors Access Control System (IMP-ACS-4DRACB) Advantages:
- Extended four-door control capability for comprehensive building security management
- Advanced multi-zone coordination with intelligent traffic flow management
- Comprehensive alarm integration with customizable alert protocols and response systems
- Scalable expansion architecture supporting future system growth and upgrades
Supporting Components:
- Metal RFID Card Reader MIFARE (IMP-ACS-MRFCR): 13.56MHz RFID reader with advanced encryption for secure credential verification
- ID Card Writer (IMP-ACS-CW): High-speed card writer with USB compatibility for efficient credential management
- 280KG Double Door Electromagnetic Lock (IMP-ACS-DDMLCK): Heavy-duty electromagnetic lock system for maximum security
- Access Control Housing with Power Supply Box (IMP-ACS-PWSH): Professional-grade integrated power supply housing with backup power capability
- Switch Panel Door Exit Push Button Access Control (IMP-ACS-MEXPBTN): Durable stainless steel exit control with LED indication
Conclusion
Advanced access control represents essential infrastructure for modern business operations. The integration of intelligent authentication, real-time monitoring, and centralized management creates comprehensive security solutions that protect assets, ensure compliance, and enhance operational efficiency.
Investment in professional business security systems provides immediate protection while establishing scalable foundations for future growth. The combination of reduced security risks, operational improvements, and regulatory compliance creates compelling ROI that justifies implementation costs.
Don’t leave your business vulnerable to security breaches and operational inefficiencies. Impulse’s advanced door access control systems provide comprehensive protection tailored to your specific requirements.


