Traditional key-based security systems are rapidly becoming obsolete in modern security infrastructure. Physical keys once the cornerstone of facility access present numerous vulnerabilities including loss, theft, unauthorized duplication, and the logistical challenges of key management across large organizations. The advent of cloud-based door access control systems represents a paradigm shift in how businesses approach security, offering unprecedented flexibility, scalability, and intelligence that legacy systems simply cannot match.
Security Vulnerabilities Demand Smarter Solutions
Security breaches cost businesses billions annually, with unauthorized physical access accounting for a significant percentage of these incidents. Traditional access systems rely on outdated technology that cannot address the complex security needs of modern enterprises:
- 67% of businesses report at least one physical security breach annually
- Key management for large facilities requires substantial administrative overhead
- Employee turnover creates significant security vulnerabilities when physical keys aren’t returned
- Traditional systems provide minimal audit capabilities and reactive rather than proactive security measures
- On-premises systems require substantial IT resources and lack disaster recovery capabilities
Cloud-based door access control systems directly address these vulnerabilities by implementing real-time monitoring, instantaneous credential management, and intelligent threat detection capabilities, all while reducing administrative burden and infrastructure costs.
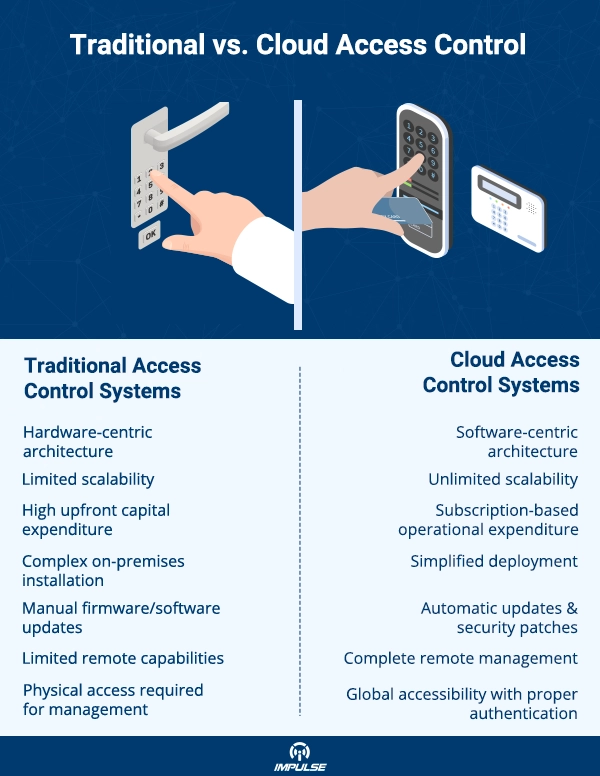
The Technical Architecture of Cloud Access Control
The technical superiority of cloud-based access control begins with its distributed architecture. Unlike traditional centralized systems that create single points of failure, cloud solutions distribute processing across multiple secure data centers while maintaining edge computing capabilities at access points.
Core Technical Components
- Edge Controllers: Devices like the TCP/IP Two Doors Access Control System and TCP/IP Four Doors Access Control System serve as intelligent edge devices within the security network architecture. These sophisticated controllers establish secure connections to the cloud infrastructure while simultaneously maintaining autonomous local decision-making capabilities that continue functioning during connectivity interruptions—ensuring uninterrupted security operations regardless of network status. The Two Doors Access Control System offers comprehensive multi-computer management for smaller deployments, while the Four Doors Access Control System extends this capability across larger installations with advanced features including:
- Regional interlocking functionality for coordinated security zones
- Fire safety linkage protocols that integrate with building safety systems
- Dynamic 2D code generation and validation for temporary access credentials
- Full cloud platform integration with centralized management capabilities
- Local processing capabilities that maintain security integrity during network outages
- Distributed intelligence architecture that prevents single points of failure
- Authentication Hardware: Modern readers like the Metal RFID Card Reader utilize sophisticated encryption algorithms operating on the 13.56MHz frequency band. This enterprise-grade MIFARE-compatible reader delivers exceptional performance characteristics essential for high-security environments where reliability and tamper resistance are paramount concerns:
- High-sensitivity detection circuits that maximize read range while minimizing power requirements
- Low power consumption design optimized for continuous operation
- Wiegand output compatibility ensuring integration with virtually any access control system
- Minimal error rates (<0.01%) even in challenging environmental conditions
- Advanced encryption for credential protection against cloning and spoofing attempts
- Ruggedized metal construction suitable for both indoor and outdoor installations
- Cloud Infrastructure: The backend system processes authentication requests, manages access policies, and provides administrative interfaces. This infrastructure typically includes:
- Redundant server architecture
- End-to-end data encryption
- Load balancing for high-traffic environments
- Database replication across geographic regions
- API gateways for third-party integrations
- Administrative Console: Web-based interfaces allow security administrators to manage the entire system remotely, including:
- Credential provisioning and revocation
- Access policy creation and enforcement
- Real-time monitoring and alerting
- Comprehensive audit reporting
- System health monitoring
Security Protocol Implementation
Cloud-based door access control systems implement multiple security layers to ensure data integrity and system reliability:
- Data Encryption: All communication between edge devices and cloud infrastructure utilizes AES-256 encryption, the same standard used by financial institutions and government agencies.
- Authentication Protocols: Multi-factor authentication ensures that only authorized personnel can access both physical spaces and administrative functions.
- Fault Tolerance: Systems like the 2 Door Access Control System and 4 Door Access Control System implement local caching of credentials and access policies, ensuring continued operation even during network outages.
- Physical Hardening: Components like the 280KG Double Door Electromagnetic Lock provide robust physical security with an innovative epoxy-less design and superior holding force exceeding 280kg of resistance, effectively securing even the most challenging entry points. Complementing this, the Access Control Housing with Power Supply Box delivers protected mounting for sensitive system components with integrated power management capabilities, ensuring consistent operation even during power fluctuations. These hardened physical components work in concert with the digital security measures to create a comprehensive security ecosystem that addresses both electronic and physical threat vectors.
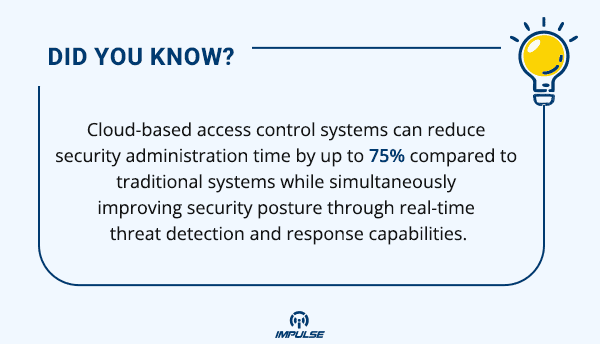
Transformative Technical Benefits for Enterprise Security
The technical advantages of cloud-based door access control translate into significant operational benefits for organizations of all sizes:
1. Enhanced Security Posture
Modern cloud-based access control systems implement security measures not possible with traditional systems:
- Real-time Credential Management: Instantly provision or revoke access rights across the entire organization.
- Suspicious Pattern Detection: Advanced algorithms identify abnormal access patterns that might indicate security threats.
- Automatic Lockdown Capabilities: Trigger immediate facility-wide lockdowns during security incidents.
- Zero-Trust Architecture: Every access request is thoroughly verified regardless of location or previous authentications, implementing the security principle that trust is never assumed but must always be validated through multiple verification layers.
2. Technical Scalability
The TCP/IP Two Doors Access Control System and TCP/IP Four Doors Access Control System controllers form the foundation of a highly scalable security architecture designed to grow alongside organizational needs:
- Modular Deployment: Begin implementation with a single door and seamlessly expand to thousands of access points across multiple geographic locations without replacing existing infrastructure. This approach allows organizations to make strategic security investments that align with budgetary constraints while maintaining a clear upgrade path for future expansion.
- Consistent User Experience: Maintain identical security protocols, credential formats, and authentication methods across all facilities regardless of size or location, ensuring that employees experience uniform access procedures whether entering headquarters or a remote satellite office.
- Centralized Management: Administer comprehensive global access policies from a single administrative interface, eliminating the need for distributed security management teams and ensuring consistent policy enforcement throughout the organization.
- Flexible Authentication: Support for multiple credential types including physical cards, smartphone-based digital credentials, PIN codes, and biometric identifiers, allowing organizations to implement multi-factor authentication strategies appropriate to each security zone’s requirements.
3. Operational Intelligence
Cloud systems provide unprecedented visibility into facility usage patterns:
- Comprehensive Audit Trails: Every access attempt is logged with timestamp, location, and credential details.
- Occupancy Analytics: Real-time and historical data on building utilization.
- Integration Capabilities: Connect with HR systems for automated onboarding/offboarding.
- Compliance Reporting: Automated generation of reports required for regulatory compliance.
4. Infrastructure Resilience
Cloud architecture provides superior reliability:
- Disaster Recovery: Automatic failover to redundant systems during outages.
- Automatic Updates: Security patches and feature enhancements without downtime.
- Remote Troubleshooting: Diagnose and resolve complex system issues without requiring expensive and time-consuming on-site technical visits. System administrators can view detailed diagnostic information, update firmware, modify configurations, and even reboot individual components remotely, dramatically reducing system downtime and maintenance costs.
- Backup Power Compatibility: Systems like the Access Control Housing with Power Supply Box provide integrated power supply solutions with sophisticated battery backup options that maintain system functionality during power outages. These power management systems include intelligent charging circuits, automatic failover capabilities, and status monitoring to ensure continuous operation during critical security events when traditional power sources may be compromised.
Implementing Enterprise-Grade Access Control with Impulse CCTV
For organizations ready to modernize their security infrastructure, Impulse CCTV offers comprehensive cloud-based door access control solutions engineered for enterprise requirements:
Core System Components
- TCP/IP Controllers: The foundation of any enterprise-grade cloud-based access control system begins with robust, network-connected controllers that serve as the system’s distributed intelligence. Impulse CCTV offers scalable controller options designed for various deployment scenarios:
- TCP/IP Two Doors Access Control System : Ideal for small to medium deployments, this sophisticated two-door controller features enterprise-class TCP/IP connectivity with advanced networking capabilities, comprehensive regional interlocking for coordinated access zones, intelligent fire safety linkage capabilities, and dynamic 2D code support for temporary credential management. Its multi-computer management functionality enables distributed administration across complex organizational structures while maintaining centralized policy enforcement.
- TCP/IP Four Doors Access Control System : Engineered for larger installations, this four-door controller delivers the same advanced features as the Two Door model but with expanded capacity and enhanced processing capabilities, making it the perfect solution for managing main entrances, high-security areas, and interconnected access zones requiring sophisticated rules and permissions.
- Physical Security Hardware: Complete your implementation with purpose-built, industrial-grade components designed for continuous operation in demanding environments:
- 280KG Double Door Electromagnetic Lock : This high-strength electromagnetic lock features an innovative epoxy-less design with either plated or anodized finish options for superior environmental resistance. Providing an exceptional holding force of 280KG, this lock delivers formidable physical security with simplified installation features including a control PCB mount assembly that streamlines wiring and configuration.
- Switch Panel Door Exit Push Button : Constructed from premium stainless steel plate, this exit button combines elegant aesthetics with exceptional durability, delivering reliable operation even in high-traffic environments where lesser components would quickly deteriorate. The tactile feedback mechanism ensures positive actuation while resisting vandalism attempts.
- Access Control Housing with Power Supply Box : This integrated solution provides protected mounting for control boards in a secure enclosure while simultaneously supplying clean, reliable power to connected devices including electromagnetic locks, readers, and auxiliary components. The built-in power management system includes surge protection, load balancing, and optional battery backup capabilities.
- Authentication Technology: Implement enterprise-grade secure credential management with these specialized components:
- ID Card Writer : This professional credential enrollment device features exceptionally fast reading and writing speeds combined with high-quality microcomputer control for precise data handling. USB compatibility ensures efficient data transmission without requiring specialized driver installation, simplifying deployment across multiple enrollment stations while maintaining data integrity.
- Metal RFID Card Reader : This industrial-grade reader operates on the secure 13.56MHz frequency band with sophisticated encryption algorithms that prevent credential cloning and replay attacks. The reader’s precision engineering delivers high sensitivity detection with extremely low error rates even in challenging installations with potential interference sources. Full support for standard Wiegand output protocols ensures universal compatibility with virtually any access control system, simplifying integration into both new and existing infrastructure.
Implementation Methodology
A successful cloud-based door access control deployment follows a structured methodology:
- Security Assessment: Comprehensive analysis of current vulnerabilities and access requirements.
- System Design: Custom-tailored hardware selection and architecture planning based on facility needs.
- Controlled Deployment: Phased implementation ensuring continuous security during transition.
- Integration: Connecting the access control system with existing security infrastructure and business systems.
- Training: Comprehensive administrator and user training on new protocols and capabilities.
- Ongoing Support: Continuous monitoring and system optimization to address evolving security needs.
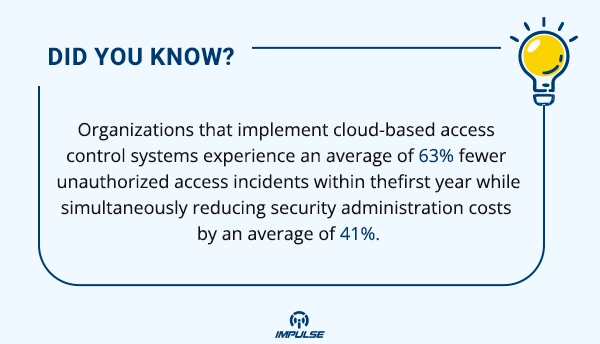
Conclusion
Cloud-based door access control represents the convergence of physical and digital security paradigms, delivering unprecedented protection, intelligence, and operational efficiency. As security threats continue to evolve, static systems will increasingly fail to provide adequate protection, while cloud-connected solutions offer the adaptability and intelligence necessary to counter emerging threats.
Impulse CCTV’s comprehensive portfolio of cloud-compatible access control components provides organizations with the technical foundation necessary to implement truly modern security infrastructure transforming physical access from a vulnerability into a strategic asset.
We supply cloud-based access control systems for your organization. Get in touch with us to learn how our security solutions can enhance your organization’s security while lowering costs.


